应用的配置中可能涉及一些敏感信息,如用户名密码,将这些信息直接容器镜像中是不合适的,明文的形式写在deployment.yaml中也容易泄露。K8s提供Secret以密文的形式存储数据,避免了直接在配置文件中保存敏感信息。对于一些非敏感信息,如应用的配置信息,可以用ConfigMap管理
Secret管理机密信息
创建Secret
1
2
3
4
5
6
7
8
9
10
11
12
| apiVersion: v1
kind: Secret
metadata:
name: mysql-secret
labels:
app: my-mysql
type: Opaque
data:
mysql-root-user: "cm9vdA=="
mysql-root-password: "MTIzNDU2"
mysql-user: "empt"
mysql-password: "MTIzNDU2"
|
Secret中data的值用base64加密 echo -n root | base64
查看secret
kubectl get secret,kubectl describe secret {secret_name}
ConfigMap管理应用配置信息
1
2
3
4
5
6
| apiVersion: v1
kind: ConfigMap
metadata:
name: mysql-cm
data:
MYSQL_PORT: "3306"
|
kubectl get configmap,kubectl describe configmap {configmap_name}
实例:用Secret与ConfigMap管理MySQL的用户名密码和配置信息
PV
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| apiVersion: v1
kind: PersistentVolume
metadata:
name: mysql-pv
spec:
capacity:
storage: 15Gi
accessModes:
- ReadWriteMany
persistentVolumeReclaimPolicy: Retain
storageClassName: nfs
nfs:
path: /home/work/nfs/mysql/
server: node1
|
PVC
1
2
3
4
5
6
7
8
9
10
11
| apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: mysql-pvc
spec:
accessModes:
- ReadWriteMany
resources:
requests:
storage: 15Gi
storageClassName: nfs
|
ConfigMap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| apiVersion: v1
kind: ConfigMap
metadata:
name: mysql-config
data:
mysqld.cnf: |
[client]
port=3306
[mysql]
no-auto-rehash
[mysqld]
skip-host-cache
skip-name-resolve
default-authentication-plugin=mysql_native_password
character-set-server=utf8mb4
collation-server=utf8mb4_general_ci
explicit_defaults_for_timestamp=true
lower_case_table_names=1
|
Deployment
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
| apiVersion: apps/v1
kind: Deployment
metadata:
name: my-mysql
labels:
app: my-mysql
spec:
selector:
matchLabels:
app: my-mysql
replicas: 1
template:
metadata:
labels:
app: my-mysql
spec:
containers:
- name: my-mysql
image: "mysql:latest"
env:
- name: MYSQL_ROOT_PASSWORD
valueFrom:
secretKeyRef:
name: mysql-secret
key: mysql-root-password
- name: MYSQL_PASSWORD
valueFrom:
secretKeyRef:
name: mysql-secret
key: mysql-password
- name: MYSQL_USER
valueFrom:
secretKeyRef:
name: mysql-secret
key: mysql-user
volumeMounts:
- name: cm-vol
mountPath: /etc/mysql/conf.d
- name: nfs-vol
mountPath: /var/lib/mysql
volumes:
- name: cm-vol
configMap:
name: mysql-config
items:
- key: mysqld.cnf
path: mysqld.cnf
- name: nfs-vol
persistentVolumeClaim:
claimName: mysql-pvc
|
Service
1
2
3
4
5
6
7
8
9
10
11
12
| apiVersion: v1
kind: Service
metadata:
name: my-mysql
spec:
ports:
- port: 3306
targetPort: 3306
nodePort: 30006
type: LoadBalancer
selector:
app: my-mysql
|
以上配置写在 mysql-deployment.yaml中,用 --- 分割
secret信息单独放在secret.yaml中
1
2
3
4
5
6
7
8
9
10
11
12
| apiVersion: v1
kind: Secret
metadata:
name: mysql-secret
labels:
app: my-mysql
type: Opaque
data:
mysql-root-user: "cm9vdA=="
mysql-root-password: "MTIzNDU2"
mysql-user: "empt"
mysql-password: "MTIzNDU2"
|
创建secret信息 kubectl apply -f secret.yaml
创建mysql应用 kubectl apply -f mysql-deployment.yaml
访问mysql服务:mysql -uroot -p123456 -Pnode1
遇到问题
mysql服务副本数设置为2,有一个Pod总是会失败
通过 kubectl logs -f {podId} -n default
查看Pod日志,发现ibdata1文件被锁住,导致Pod中的mysql进程无法启动,看来不能以2个主节点的形式部署mysql集群,应是一主多从,该如何用k8s部署?(如何用k8s部署高可用的mysql集群)
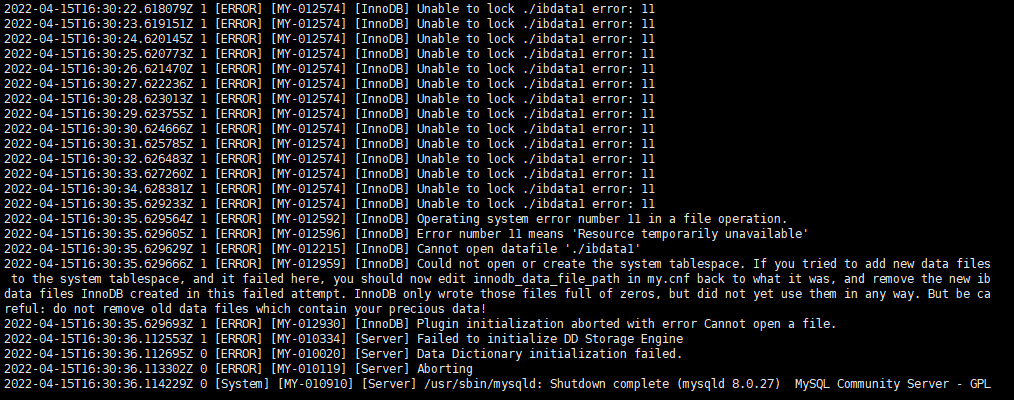 image-20220416003709230
image-20220416003709230
